Cybersecurity is now the crux of the matter
Political and industrial espionage
Ransom demand via ransomware
Reputational damage
Destruction of information assets
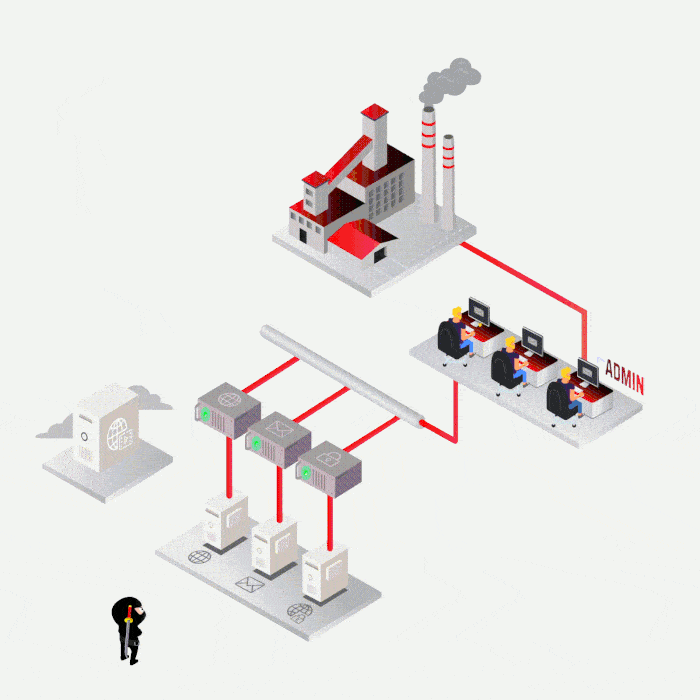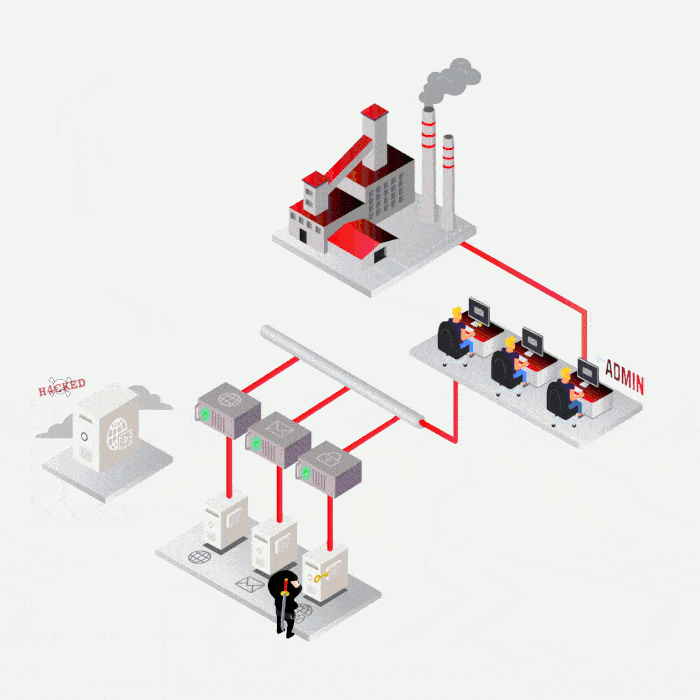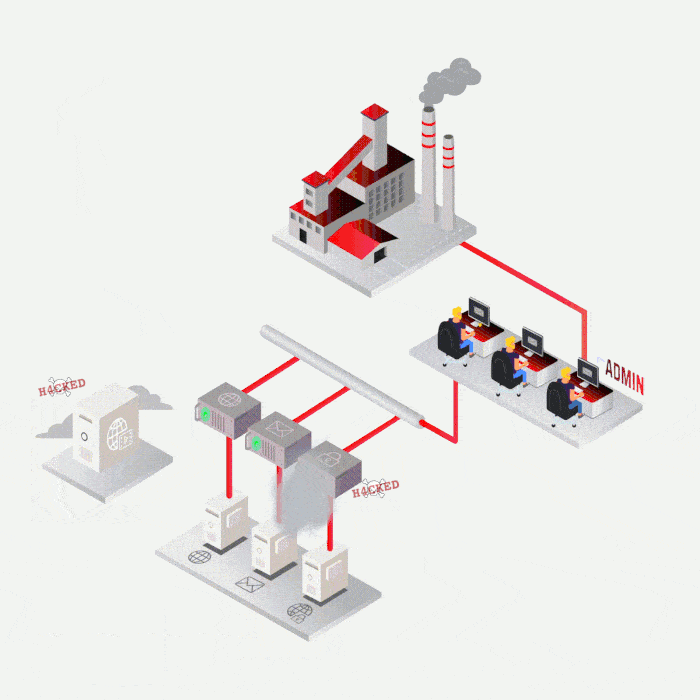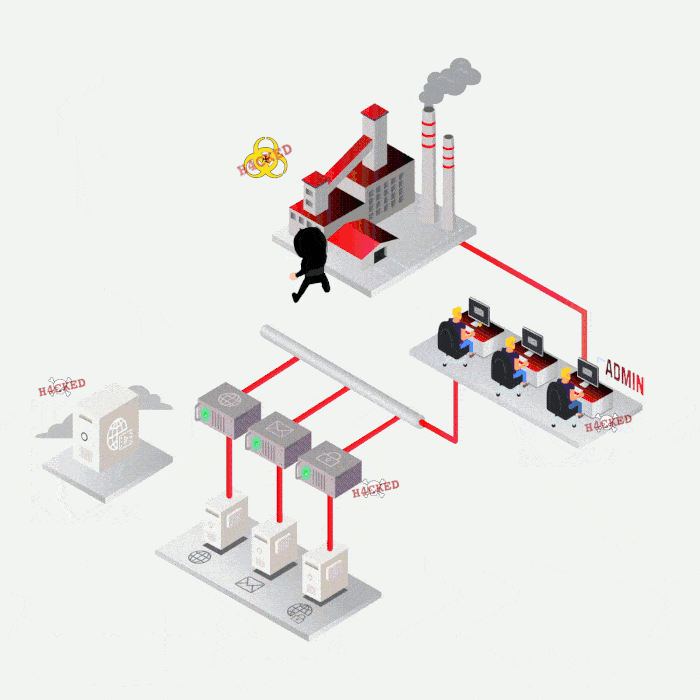
Case study
Most frequent cases
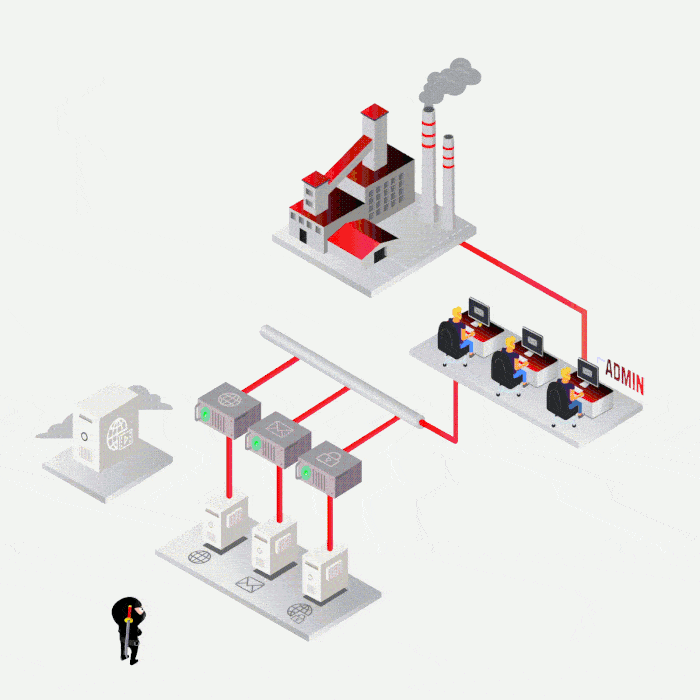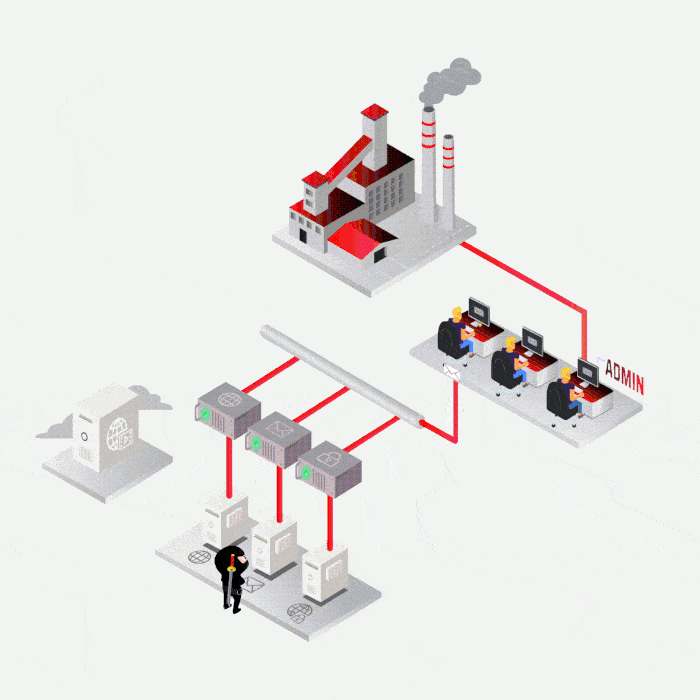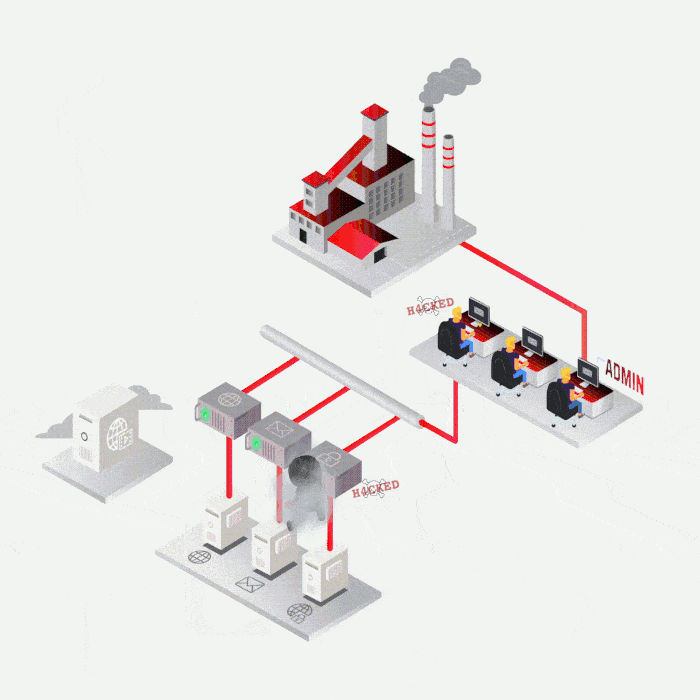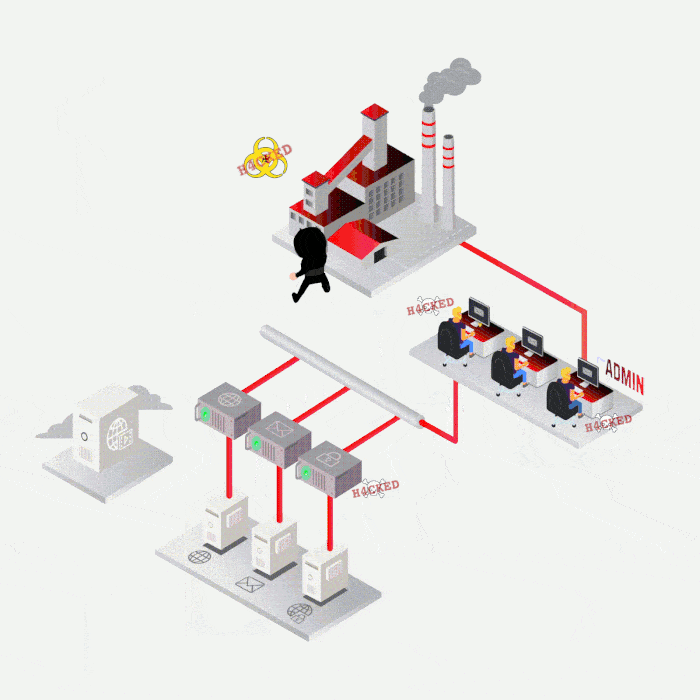
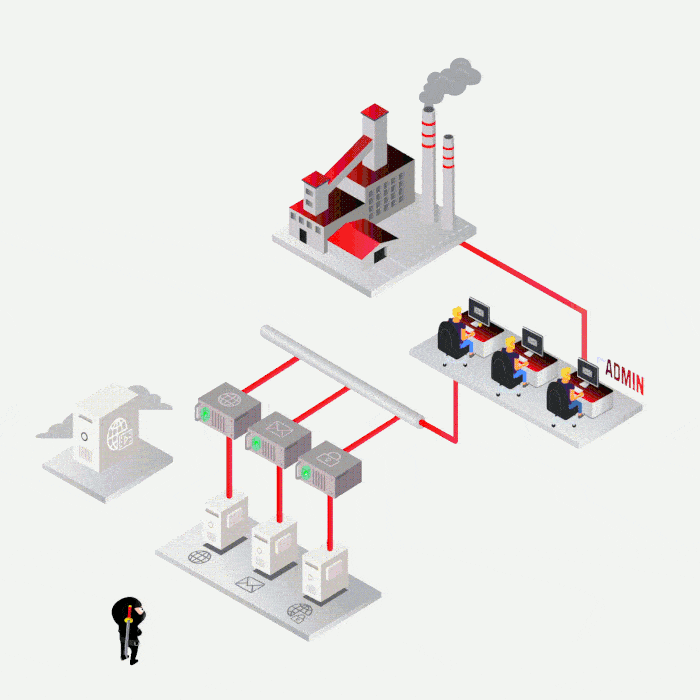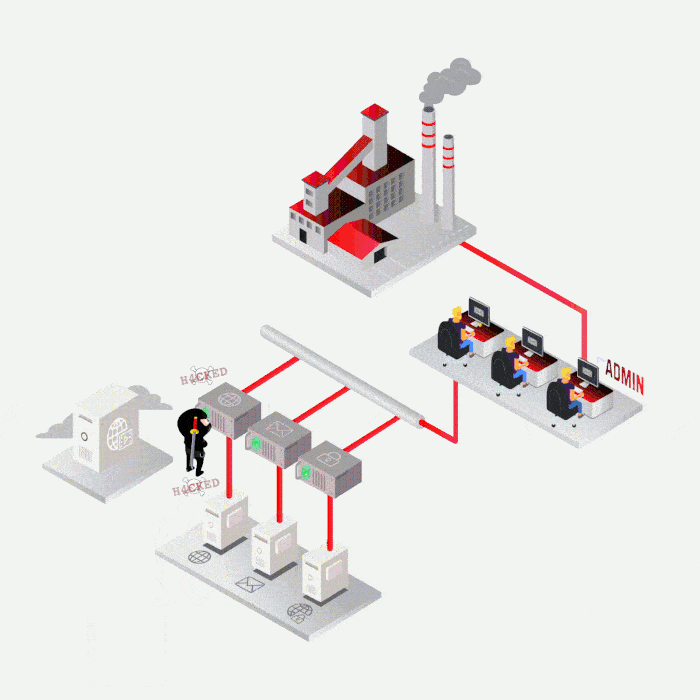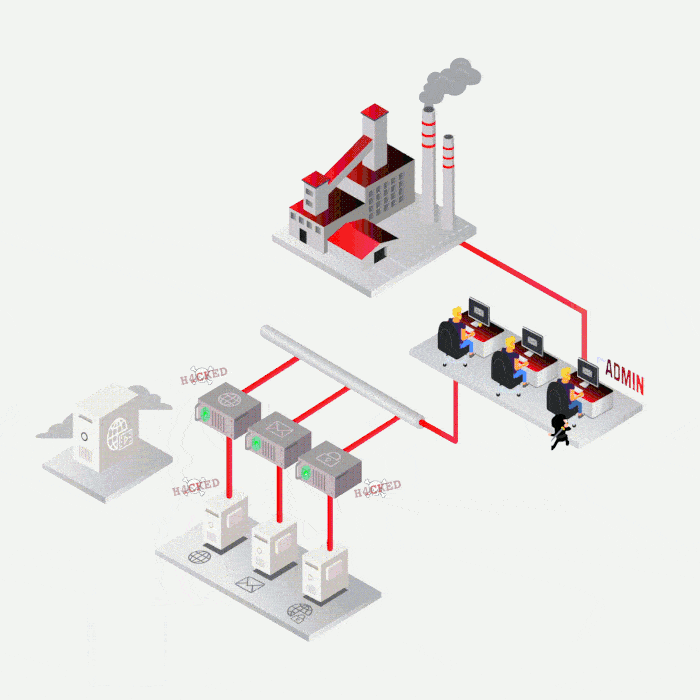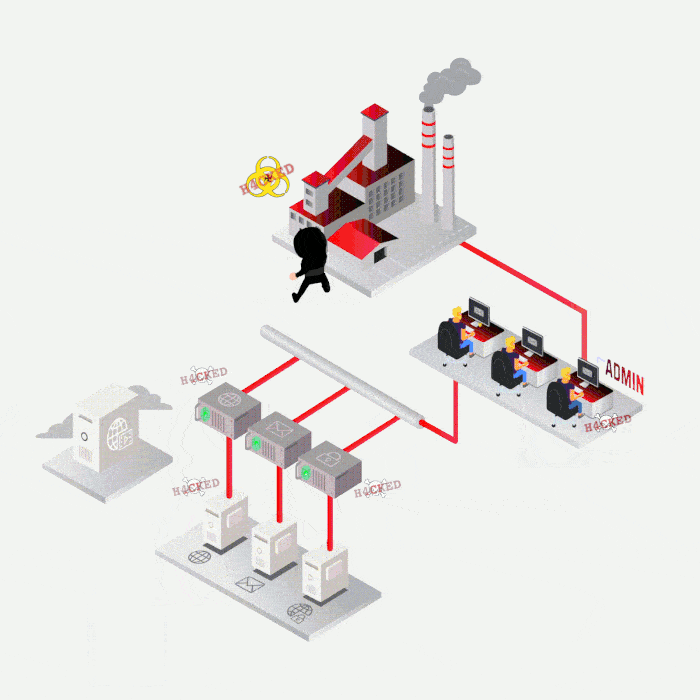
SYNACKTIV, A GUARANTEE OF TECHNICAL EXPERTISE
At Synacktiv, we make it a point of honor to ensure our clients' satisfaction. Such a result can only be achieved through state-of-the-art technical expertise and a thorough understanding of today's threats. Because we strive for constant improvement, we take part in international conferences and "Capture the Flag" competitions to perfect our knowledge and intrusion techniques.
Testimonials

Sébastien Gaïde

Marc-Antoine Lacroix