Oursin
Spear phishing attack platform
OBJECTIVES
- Facilitate the implementation of efficient spear phishing campaigns during Red Team intrusion tests
- Reduce the time needed to set up backdoors
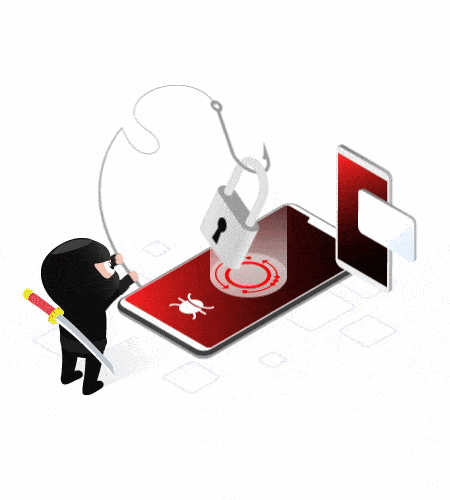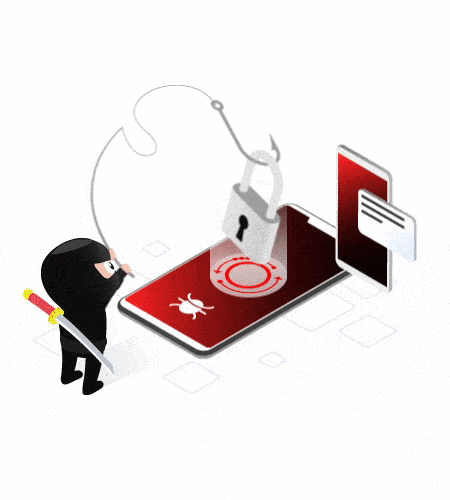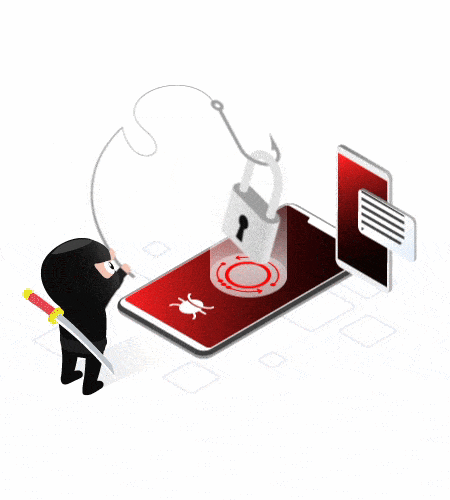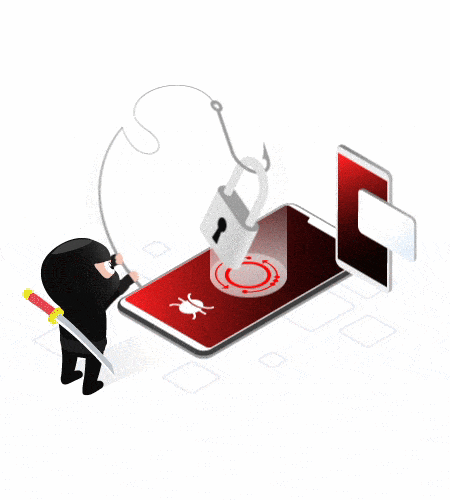
Innovations
Custom scenarios - Multiple attack vectors
Modular payloads - Custom backdoors
Modular payloads - Custom backdoors
Functionalities
CUSTOM SCENARIOS
Email template editor via the web interface
Payload customization
MULTIPLE INTRUSION VECTORS
Sending emails containing malicious links or attachments
Setting up website copies automatically
Generating payloads for use on rigged USB sticks
MULTIPLE PAYLOADS
Browser exploits, Office macros, Java applets, etc.
Modal architecture, quick addition of new payloads
CUSTOM BACKDOORS
Command execution, file upload and download
Development in Python
Antivirus bypass
Setup of a SOCKS server, lateral movement to compromise the local network
Multiple output protocols (TCP, SSL, HTTP, DNS)
CAMPAIGN MONITORING
Integrated dashboard
Advanced statistics regarding the number of clicks, successful exploits, technologies in use (operating systems, browsers, plugins) and user geolocation
Feedback about the vulnerabilities affecting the workstations
Customer Experience
Without Oursin
- Tedious spear phishing campaign setup
- Single-use email templates and developments
- Manual generation of payloads: unproven reliability
- Backdoor development or public code reuse: antivirus detection
With Oursin
- Automation of tedious tasks. Focus on the scenarios chain and on post-exploitation
- Multiple predefined scenarios accessible to the user in a few clicks
- Possibility to copy or modify existing scenarios
- Automatic generation of a payload chosen among a set of reliable loads
- Custom, well-tested backdoor, unknown of antivirus software
