DJI Pilot Android Application Security Analysis
We also studied DJI Pilot, the application dedicated to professionals and companies, in order to assess its security and look at the difference between the two apps.
We found similar issues to those listed in our previous blogpost in this application, such as a forced update mechanism.
Looking to improve your skills? Discover our trainings sessions! Learn more.
In our previous analysis, we studied the DJI GO 4 application 1 , dedicated to the consumer grade drones.
The New York Times covered our analysis 2 and quoted DJI response to our publication which pointed that our previous findings were not applicable to DJI Pilot, the professional mobile application for flying DJI Enterprise aircrafts.
Following this statement, we decided to assess the security of DJI Pilot.
This application is used, for example, to control the DJI Matrice, Phantom 4, Mavic Pro and Mavic 2 Enterprise aircrafts.There is evidence that these drones are used over sensitive areas such as some French Gendarmerie barracks 3 and were used during the lockdown in France 45.
We found out that the forced upgrade mechanism found on DJI GO 4 is also present in the DJI Pilot application, and that their “offline” mode requires a network connection in order to unlock flying over sensitive areas.
Key Findings
- The professional DJI Pilot application is protected using the same packer as the consumer grade DJI Go 4 application
- The professional DJI Pilot application includes the same forced upgrade mechanism as the one present in its consumer grade applications
- The “offline” Local Data Mode requires an Internet connection in order to install unlocking certificates
We encourage the reader to read our previous blog post which give further technical details on the identical findings to the ones in DJI GO 4.
Test Setup
The testing setup used is the same as our previous analysis:
- A rooted Android 9 phone
- WiFi Connection over a controlled Access Point
- Burp6 setup to intercept communications
- Frida7 scripts for unpacking and SSL pinning bypass
- JADX8 for static analysis
We analyzed several revisions of the application on the Android platform, namely:
- The official V1.8.0 release from Google Play Store, updated on June 11, 2020 (SHA256:
5d63effeaa19c2c70e22b868e27dbabee2aeb5a5248b433c2b9591705640825d) - V1.8.0 (SHA256
6476c6a715be37522d770af5ea1ae77bcaedcc542bdec45fc842f3250acc9d9c, filename1591844954295-djipilot-Official-release-v1.8.0-25415-20200610-25961-1336.apkupdated on June 11, 2020 ) - V1.7.2 (SHA256
99664e71bdb8032faf2eeda63ba64b1a662d365d8216e8d42b815e15d6828c5b/ filenamecom.dji.industry.pilot_v1.7.2-20568_minAPI21(arm64-v8a,armeabi-v7a).apkupdated on March 13, 2020)
Application unpacking
The application is protected using the same packer (SecNeo) as the consumer grade one:
- The main code is contained in several encrypted Dex files.
- A stub in an obfuscated library named
libDexHelper.sois in charge of dynamically decrypting and loading the Dalvik bytecode into memory. It should be noted that only the parts of code used are loaded. - Depending on the release, the strings are either in cleartext or encrypted using the same XOR based algorithm with the same key.
Therefore, we could analyze the application using the same tools and methodologies as the ones used during our analysis of DJI GO 4.9
Forced upgrade mechanism
The forced upgrade mechanism found on the DJI Go 4 application for Android is present in the DJI Pilot application provided on their website 10. While some of the code is present in the application distributed through Google Play Store, the application redirects to the DJI Pilot application page on the store when forced to upgrade. The rest of this analysis was done on the application distributed by DJI on their official website 10
As a reminder, this mechanism is proprietary and can be configured in a “forced update” mode in which the user cannot pilot the drone using the app unless they accept the update installation.
During startup, or if the users checks for an update, the application makes the following request:
POST /app/upgrade/public/check HTTP/1.1
adhoc-sign: REDACTED
Content-Type: application/json; charset=UTF-8
Content-Length: 167
Host: service-adhoc.dji.com
Connection: close
Accept-Encoding: gzip, deflate
User-Agent: okhttp/3.11.0
{
"appKey": "djipilot",
"appStatus": "release",
"language": "en_us",
"packageName": "com.dji.industry.pilot",
"platform": "android",
"versionCode": "25415",
"versionName": "v1.8.0"
}
The server response is similar to the one observed during DJI GO 4 analysis:
HTTP/1.1 200
Server: Tengine
Content-Type: application/json;charset=UTF-8
[...]
EagleId: REDACTED
Content-Length: 209
{
"code": 0,
"message": "无符合条件的升级包",
"data": {
"update": "false",
"downloadUrl": null,
"isForce": null,
"newVersionName": null,
"newVersionCode": null,
"log": null,
"md5": null,
"fileSize": null,
"releaseTime": ""
}
}
Given the similarities between the update mechanisms, we were able to force the user to install an arbitrary application using the same tools and methology as DJI GO 4. It should be noted that if the isForce field is true, the message will be blocking the user.
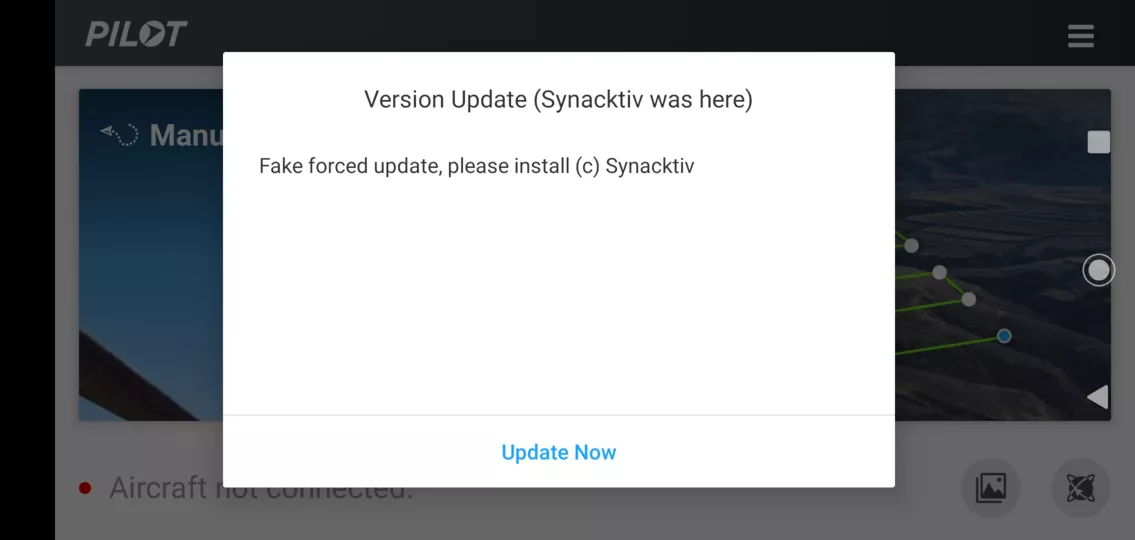
A last warning is displayed to the user before installing the arbitrary application already downloaded.
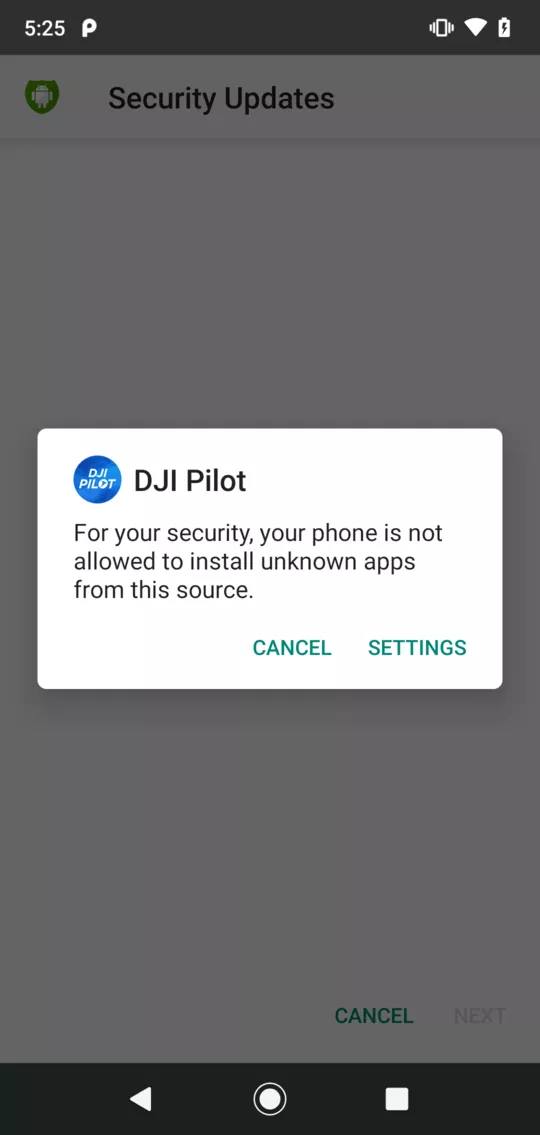
This mechanism is very similar to command and control servers encountered with malwares. Given the wide permissions required by DJI Pilot (access contacts, microphone, camera, location, storage, change network connectivity, etc.), the DJI servers have almost full control over the user’s phone.
Weibo SDK
The Weibo SDK identified in the DJI GO 4 application is also contained in some releases of this application. Among the versions we analyzed, version 1.8.0 downloaded from the Play store did not have this feature, but the version 1.8.0 downloaded on DJI Website did. When distributed, this SDK includes the AppInstallCmdExecutor class which is able to download an arbitrary APK application. In the same fashion as in DJI GO 4 application, the Weibo SDK collects a handful of personal identifiers, including IMSI, IMEI, or the SSID of the local WiFi network 11.
It should also be noted that the update mechanism in the Weibo SDK is made over HTTP, which is insecure and prone to a Man in the Middle attack. Such an attack would allow a third party attacker to modify the server answer and trigger the installation mechanism without the knowledge of Weibo.
As noted by Grimm Security in their confirmation of our analysis of DJI GO 4 11, this SDK is also included in several other applications.
Local Data Mode
DJI did advertise a specific “disconnected” mode for its DJI Pilot application, named “Local Data Mode” 12, which is supposed
to stop Internet traffic from the application.
This mode can be activated in the DJI Pilot application using a settings in the application configuration menu.
However, activating this mode will disallow features needed for certain types of sensitive missions, such as unlocking fly zones, as will be seen in the following screenshot.
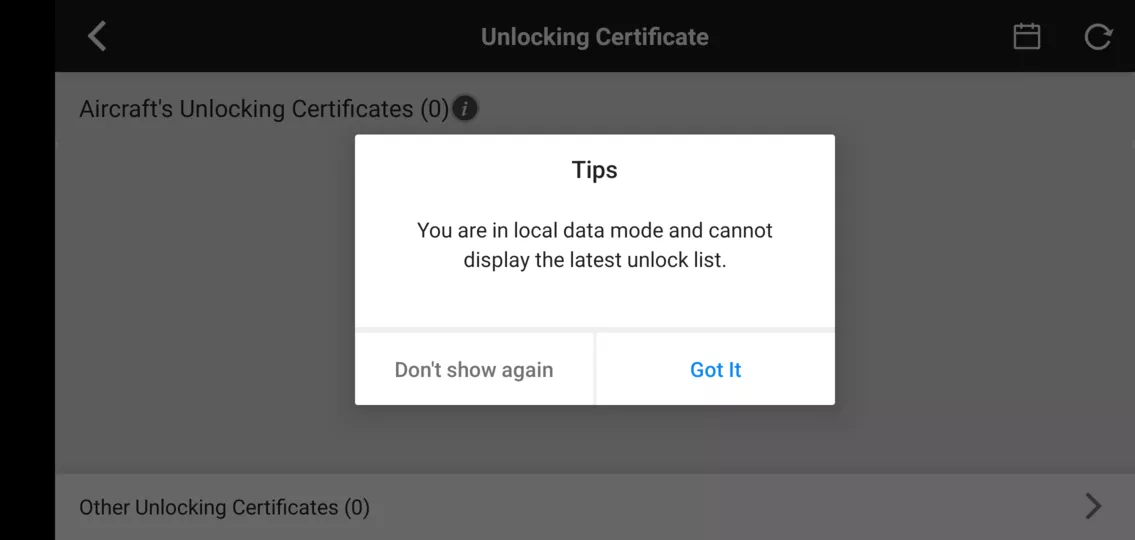
To use these functionalities, a user thus has to deactivate this mode, allowing network communications during a certain amount of time. If the user does this, his or her device is prone to Forced Update as mentioned before.
Moreover, to unlock flying in restricted airspace, a user has to ask DJI for permission using their process 13 and will be delivered an unlock certificate linked to their aircraft and user account.
Because the certificate registration is linked to the user's account, it may allow specific targeting of sensitive users.
Recommendations
To mitigate the risks presented in this blogpost, we recommend to keep the application updated, and to check that the update
comes from the official Google Play Store.
Conclusion
The same type of security concerns about the DJI GO 4 application do apply to DJI Pilot, the professional version of the application, and therefore we advise not using it for sensitive purposes.
- 1. DJI ANDROID GO 4 APPLICATION SECURITY ANALYSIS
- 2. Popular Chinese-Made Drone Is Found to Have Security Weakness
- 3. Débloquer une No Fly Zone sur DJI Pilot
- 4. Le drone, renfort utile mais controversé pour faire respecter le confinement
- 5. Coronavirus : pour faire respecter le confinement, les gendarmes de Lorraine utilisent un drone
- 6. Burp
- 7. Frida
- 8. JADX
- 9. Unpacking
- 10. a. b. DJI Pilot Download Center
- 11. a. b. DJI Privacy Analysis Validation
- 12. DJI Launches Privacy Mode For Drone Operators To Fly Without Internet Data Transfer
- 13. DJI FlySafe
